Ransomware: A How-To Guide
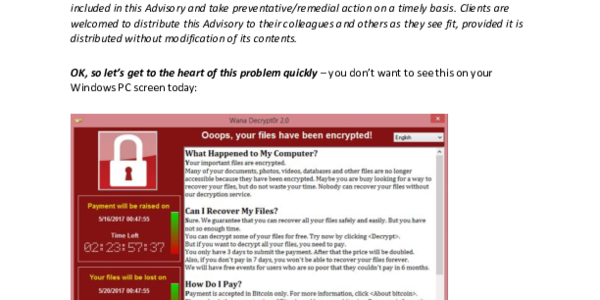
Other - Law Firms | 03/06/2017Some forms of cyber extortion are automated and not targeted at any specific victim. For example, "ransomware" refers to a type of malware that prevents users from accessing their systems unless, and until, a ransom is paid. Although variants of ransomware operate differently many encrypt the contents of a victim's hard drive using asymmetric encryption in which the decryption key is stored on the attacker's server and is available only after payment of the ransom. Victims typically discover the ransomware when they receive an on-screen message instructing them to transfer funds using an electronic currency, such as bitcoin, in order to receive the decryption key and access to their files. "CryptoLocker" is the most famous ransomware family and first appeared in 2013.
In November 2016, the FTC issued guidance for businesses on how to avoid and respond to ransomware attacks in its How to defend against ransomware 1 and Ransomware - A closer look. 2
To read more, please log in
Featured